math jokes 4 mathy folks
live. laugh. learn.
With your mouse, click and drag one of the images below so that it aligns exactly with the other image. When the images are aligned, a hidden number will appear. If you can't see the hidden number, then the images are not aligned — try again.


The original image used to create this encryption is shown at the bottom of this page. Scroll down now if the anticipation is more than you can bear.
The technique used to create the two images above is rather simplistic, but it took the genius of Moni Naor and Adi Shamir to realize that it could be done. Each pixel in the original image is replaced by four smaller pixels in the two encryption images. Of these four smaller pixels, two of them are colored black, and two are colored white. Now, here was the genius of Naor and Shamir — they realized that if you colored the same two pixels black in both encryption images, the combination would appear gray when the images are overlaid; on the other hand, if you colored two different pixels black in the encryption images, the result would appear black when overlaid.
The two examples below show this process in action. When the same two pixels are colored black, the combination is only half-colored, which gives the appearance of gray when the images are overlaid:
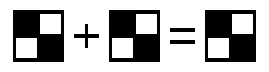
But when different pixels are colored black, the combination is entirely colored, which gives the appearance of black when the images are overlaid:
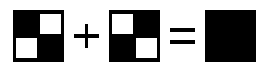
One by one, this wouldn't have much of an effect. But when all of the pixels of the original image are divided and colored in this manner — as all of the 630 pixels in the image below were, to create the encryption images above — the result is quite effective.

Moni Naor and Adi Shamir pioneered visual cryptography in 1994.
In cryptography, secret sharing is any method that allows a secret to be divided into parts ("shares"), and several people are each given
a share. By themselves, these shares are of no use; the secret can only be reconstructed when all of the shares are combined.
That's the idea behind the visual cryptography example seen here. Each of the images to the right, by itself, is meaningless. But when combined —
in this case, placed one on top of the other — a secret number is revealed.
The original paper by Naor and Shamir gives extensive details on how the encryption is done.